Bluesky's Data Blues: User Credentials Exposed in Plain Sight via OSINT
By George News Staff
In our ongoing series exposing the alarming vulnerabilities in how major websites handle user data, we’ve previously uncovered critical security lapses at The Atlantic, JoeBiden.com, and Der Spiegel. These investigations revealed how sensitive personal identifiable information (PII)—including emails, passwords, and login details—was stored insecurely, often in plain text or easily accessible formats, putting users at risk of identity theft, phishing attacks, and worse. Today, we turn our attention to Bluesky, the decentralized social media platform that’s positioned itself as a fresh alternative to X (formerly Twitter). Unfortunately, our findings suggest that Bluesky’s approach to data security is anything but blue skies ahead.
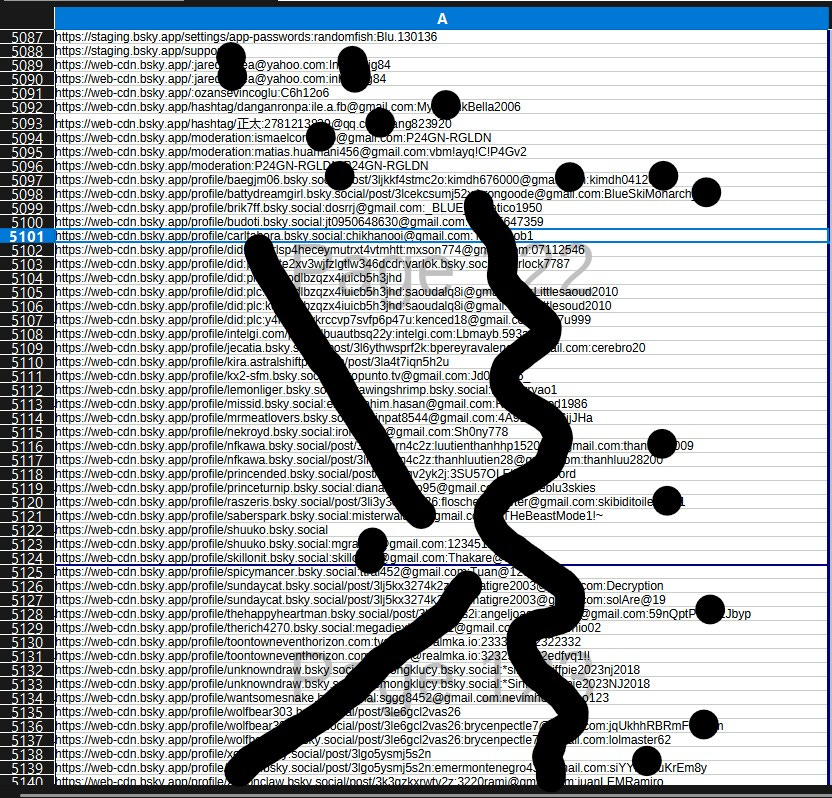
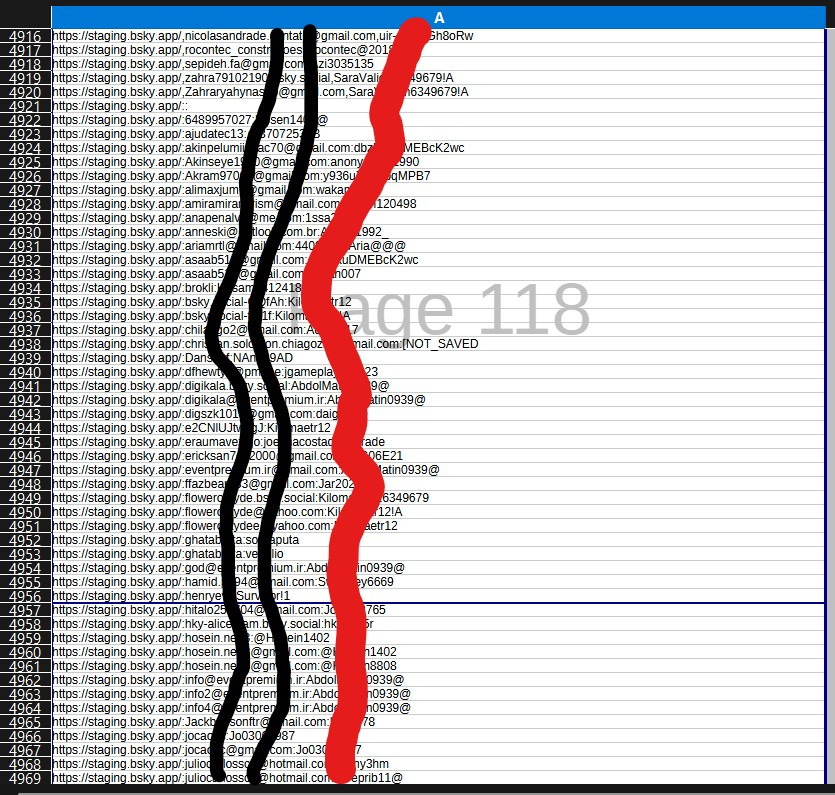
Using freely available open-source intelligence (OSINT) tools—resources accessible to anyone with basic technical know-how—we obtained (were sent) a dataset that appears to contain ten’s of thousands of Bluesky user credentials. This data, compiled in a PDF document we’ve reviewed, includes login URLs, email addresses, usernames, and associated passwords for accounts on bsky.app. The entries follow patterns like “https://account.bsky.app/signin:email:password“ or variations thereof, suggesting these are direct sign-in attempts or stored authentication details. While we won’t reproduce the full dataset here to avoid further exposure, the sheer volume and nature of the information paint a troubling picture of inadequate protection. The information that we received also had proof that these are current and “usable” PII.
The Exposed Data: A Snapshot of Vulnerability
A cache of data was sent to us, along with the method by which it was freely obtained—including proof of its authenticity—that lists an extensive array of entries. Over 100,000 by our count—detailing apparent Bluesky account credentials. These include:
Email Addresses and Passwords: Numerous Gmail, Hotmail, Outlook, and other provider emails paired with passwords ranging from simple alphanumeric strings (e.g., “123456789”) to more complex ones incorporating symbols and dates. Many passwords appear weak or reused, such as birthdates, common words like “password” or “qwerty,” and even references to pop culture or personal interests.
Usernames and Handles: Entries tied to Bluesky-specific handles like “bsky-social-XXXXX,” indicating these are platform-issued identifiers. Some include full sign-in paths, such as “https://bsky.app/:username:password.”
International Scope: The data isn’t limited to one region; emails from domains like .br (Brazil), .de (Germany), .jp (Japan), and .com (global) suggest a worldwide user base is affected. This highlights the global risks when platforms fail to secure data properly.
What’s particularly concerning is that this information was not obtained through sophisticated hacking or insider access. Instead, it surfaced via standard OSINT methods—public searches, data aggregators, and leak monitoring tools that anyone can use for free. This means cybercriminals, identity thieves, or even casual snoopers could stumble upon or actively seek out similar datasets.
In an era where data breaches are rampant, storing or allowing credentials to be exposed in this manner violates basic cybersecurity principles, such as hashing passwords (converting them into unreadable strings) and encrypting sensitive information.
Echoes of Past Exposures
This Bluesky revelation echoes the patterns we identified in our prior reports:
The Atlantic’s Unsecure Setup: As detailed in our piece on Jeffrey Goldberg’s outlet, user data was left vulnerable due to outdated security protocols, exposing emails and potentially linked personal details.
JoeBiden.com’s Safety Shortcomings: The campaign site for the current U.S. President showed similar issues, with PII stored in ways that could be easily scraped or breached, raising questions about political data handling.
Der Spiegel’s Cheap Tricks: The German publication’s hit piece on us inadvertently spotlighted their own lax data practices, where user information was not adequately shielded from public view.
Bluesky, backed by Twitter co-founder Jack Dorsey and emphasizing user control through decentralization, should theoretically prioritize privacy. Yet, this dataset suggests otherwise. If credentials are leaking into public OSINT spaces, it points to potential flaws in how the platform manages authentication, perhaps through unencrypted logs, third-party integrations, or user-submitted data that’s not properly sanitized.
The Risks: From Phishing to Identity Theft
The implications are severe. Exposed email-password pairs can lead to:
Account Takeovers: Attackers could log in directly, post misinformation, or access private messages.
Credential Stuffing: Users who reuse passwords across sites risk breaches on email, banking, or other accounts.
Phishing Amplification: Knowing a user’s email and password patterns makes targeted scams more effective.
Broader Privacy Erosion: In a platform like Bluesky, which attracts journalists, activists, and public figures, such exposures could chill free speech or enable harassment.
Bluesky’s team has touted their AT Protocol for better data portability and control, but if basic PII isn’t secured, these features become liabilities. We’ve reached out to Bluesky for comment on these findings and will update this article if they respond.
A Call for Better Data Stewardship
As we’ve stressed in our series, websites—especially those handling user interactions—have a responsibility to protect PII. Simple steps like enforcing strong password policies, using multi-factor authentication (MFA), and regularly auditing data storage could prevent these issues. Users, too, should enable MFA where available, use password managers, and monitor for breaches via services like Have I Been Pwned.
At GEORGE NEWS, we’re committed to holding platforms accountable. This isn’t about sensationalism; it’s about safeguarding the digital ecosystem we all rely on. If you’ve experienced data issues with Bluesky or other sites, share your story securely via our tips line.
Stay vigilant, and remember: In the world of online security, what you don’t know can hurt you.
This article is part of our ongoing investigation into website data vulnerabilities. Read the full series: The Atlantic, JoeBiden.com, Der Spiegel.
THANK YOU FOR YOUR SUPPORT OVER THE YEARS! If you’re reading this via a free subscription, please consider supporting us by upgrading to a (one-time) yearly subscription. If you do this by 11:59pm EDT on November 15th, 2025, we’ll UPGRADE you to a LIFETIME subscription!