The 'Manage My Health' Cover-Up: Ignored Warnings, and the Erosion of Trust in Digital Health – Part 5
By George News Staff
Welcome back to our ongoing series exposing the slippery slope of mandatory digital systems and the vulnerabilities they introduce into our lives. In Part 1, we first mentioned New Zealand’s ‘Manage My Health App’ security concerns. We also laid out the broader risks of government-mandated digital IDs and health apps, drawing from real-world examples like New Zealand’s push toward centralized data platforms. Parts 2 through 4 dove deeper into the mechanics of these systems, the profit motives behind them, and the human cost when they fail.
Why are we so interested in what happens ‘down-under’, in little ol’ New Zealand you ask? Well, for one, they’re our Five Eyes ally. And two, they’ve been a ‘test case’ population for us, going back to the early 1980’s with the likes of “EFTPOS”, and other emerging tech. It pays to pay attention.
Now, in Part 5, we’re zeroing in on what may be New Zealand’s most egregious data breach scandal yet: the Manage My Health (MMH) app fiasco. This isn’t just your typical ‘run-of-the-mill’ story about technical glitches—it’s a tale of willful ignorance, corporate deception, and potential government complicity that covers 7 months of unheeded warnings.
As whistleblowers and independent investigators, we’ve been on this since June 2025, when our team at George News received explosive intel from a source using the handle “FVEY25” (an obvious nod to the Five Eyes intelligence alliance, of which New Zealand is a member).
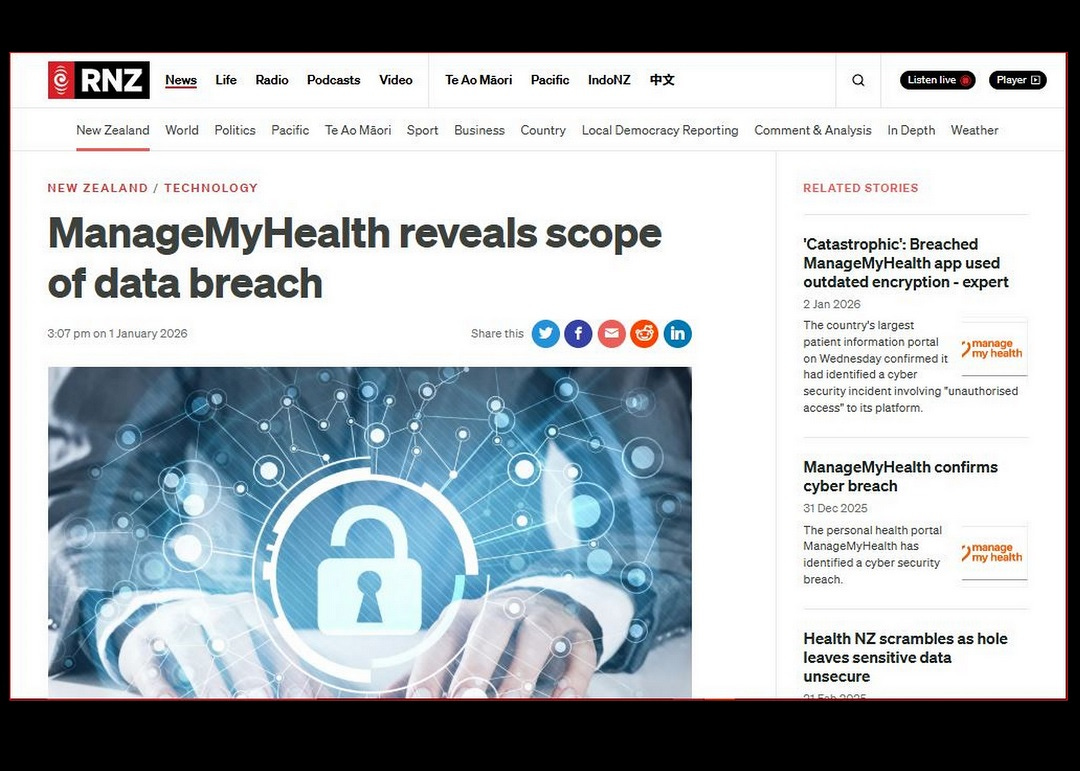
What started as a tip about exposed personal data ballooned into evidence of a massive breach affecting potentially hundreds of thousands of Kiwis. But here’s the kicker: MMH and New Zealand authorities claim the breach was only discovered on December 31, 2025.
That’s absolutely incorrect! Some may call it a “flat-out lie”.
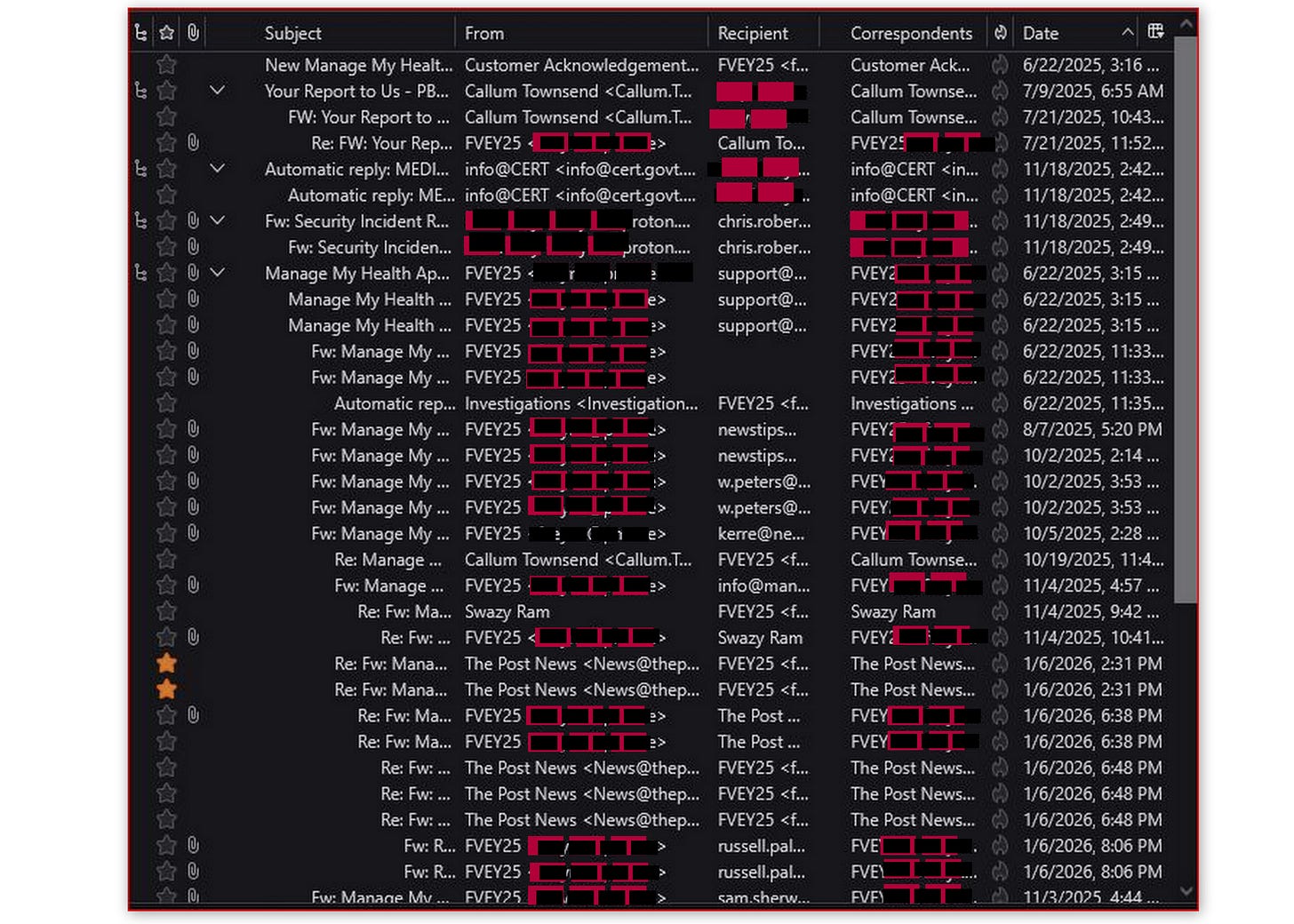
We have the emails—dozens of them—proving they were alerted as early as June 22, 2025. And despite pleas to media outlets, politicians, the Privacy Commissioner, and even the New Zealand Prime Minister’s office, via his private and personal comms, the response was crickets... or worse, deflection.
This breach isn’t minor. We’re talking many thousands of personally identifiable information (PII) records—email addresses, passwords, and potentially linked health data—exposed via third-party search engines which we cannot name here, but are mentioned in the raw EML files.
It’s the kind of leak that could enable identity theft, medical fraud, or even targeted scams. In a country pushing for digital driver’s licenses and national IDs, this should be a wake-up call. Instead, it smells like a cover-up. Let’s break it down, using the raw email evidence provided by our whistleblower, ‘FVEY25’.
The Initial Alert: June 22, 2025 – A Whistleblower Sounds the Alarm
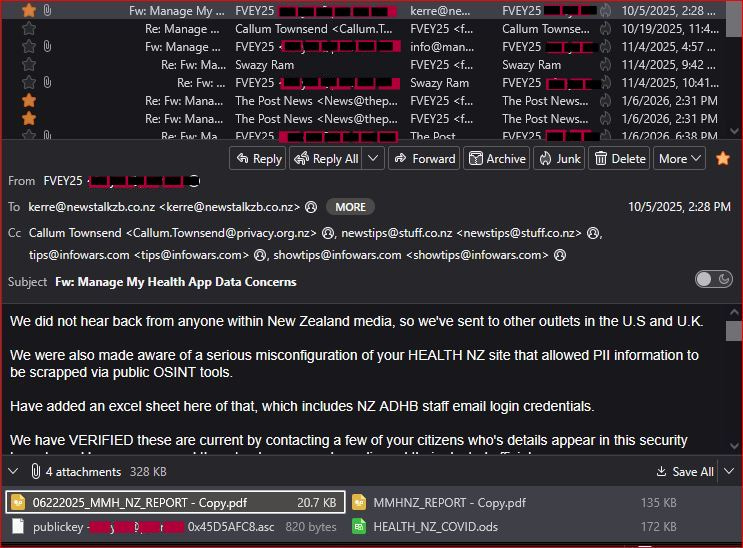
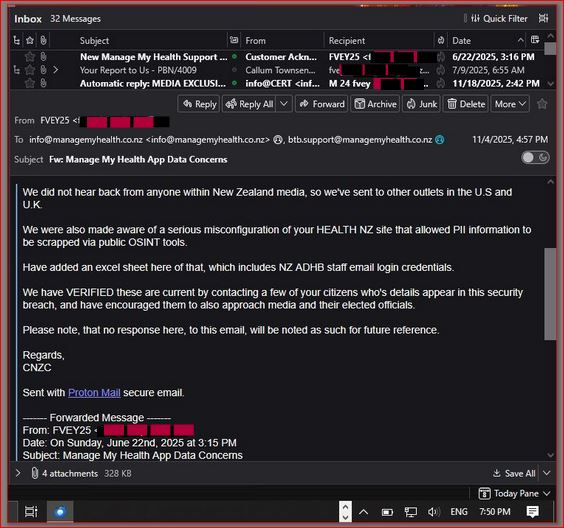
It all began with an email from FVEY25 titled “Manage My Health App Data Concerns,” sent at 3:15 PM NZST on June 22, 2025. Addressed directly to MMH support ([email protected]) and the Office of the Privacy Commissioner ([email protected]), with a BCC to New Zealand Prime Minister Christopher Luxon, via his personal and private comms. The message detailed a “significant data exposure incident.”
It referenced a 52-page PDF documenting exposed PII, including emails and passwords, scraped from MMH’s authentic site—not a phishing clone. Full-string URLs, starting mostly with messy “http” links, contained thousands of individual PII credentials.
Key quote from the initial alerting email: “These records have not come from a ‘phishing’ site, but from the authentic website in question. Discovered on June 22, 2025, and reported as of 07:00 AM NZST, June 23, 2025, immediate action is recommended... This report is submitted within the 72-hour regulatory deadline under the Privacy Act 2020.”
This single email went to 2 recipients in the ‘To’ field and 1 in BCC, alerting the company, the privacy watchdog, and the Prime Minister, Chris Luxon himself. Attached were PDFs like “06222025_MMH_NZ_REPORT - Copy.pdf” and a PGP public key for secure follow-up. MMH auto-responded with a case number (CAS-2592268), but no substantive action followed immediately.
The Privacy Commissioner’s office? They sent an automated reply acknowledging receipt but warning they might not respond if not directly addressed. Spoiler: They didn’t—at least not meaningfully at first.
Escalation and Forwards: June to August 2025 – Pleas to Privacy Officials and Media Fall Flat
By June 22 evening (11:33 PM EST equivalent), FVEY25 forwarded the original alert to four senior Privacy Commissioner staff: Blair Stewart, Katrine Evans, Annabel Fordham, and Joy Liddicoat. That’s 4 recipients, emphasizing the urgency to those tasked with protecting Kiwis’ data.
No response? Undeterred, on July 9, 2025, Callum Townsend from the Privacy Commissioner’s office followed up under reference PBN/4009, asking for clarification on potential financial fraud links. FVEY25 replied, providing more details and attaching the full PDF report. But by July 21, Townsend emailed again: “I’m just following up on the below. I don’t believe we’ve received a reply...”
This pattern of slow-walking continued. On August 7, 2025, FVEY25 forwarded the alert again, this time to an even broader audience, including media and officials.
October 2025: Media Blackout and Health NZ Misconfigurations Exposed
Things heated up in October. On October 2, 2025 (3:53 AM EST), FVEY25 forwarded the original to Newstalk ZB hosts and news desks: Kerre, Kerrie, Leighton, Mike Hosking, Mike, and the general news inbox—over 100 media staff combined. No reply.
Later that day (2:14 AM EST), another forward to Newstalk ZB staff, expanding to Richard, Steff, Ian Johnston, Justin, John D, and more—a staggering 100+ in CC, pleading for coverage. Still nothing.
By October 5, 2025, FVEY25 escalated to Newstalk ZB again, attaching an Excel sheet exposing a separate Health NZ misconfiguration leaking ADHB staff credentials.
This email went to 6 media contacts in ‘To’, CC’d to the Privacy Commissioner’s Callum Townsend, Stuff NZ tips, and even Infowars ([email protected] and [email protected]).
The message: “We have VERIFIED these are current by contacting a few of your citizens... and have encouraged them to also approach media and their elected officials.”
On October 19, Townsend responded tepidly: “Thank you for the information provided. OPC are assessing... We’ll be in touch if we have any further questions.” But no action was visible.

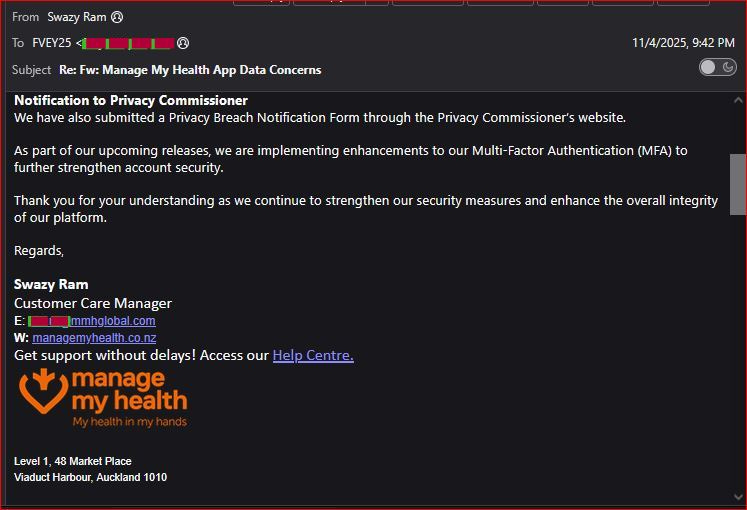
November 2025: MMH’s Half-Measures and More Ignored Forwards
November brought a response from MMH’s Swazy Ram on November 4, claiming proactive steps: password resets, 2FA enforcement, and a Privacy Breach Notification. But this was months after the initial alert—sent to 1 recipient (FVEY25), it felt like damage control, not prevention.
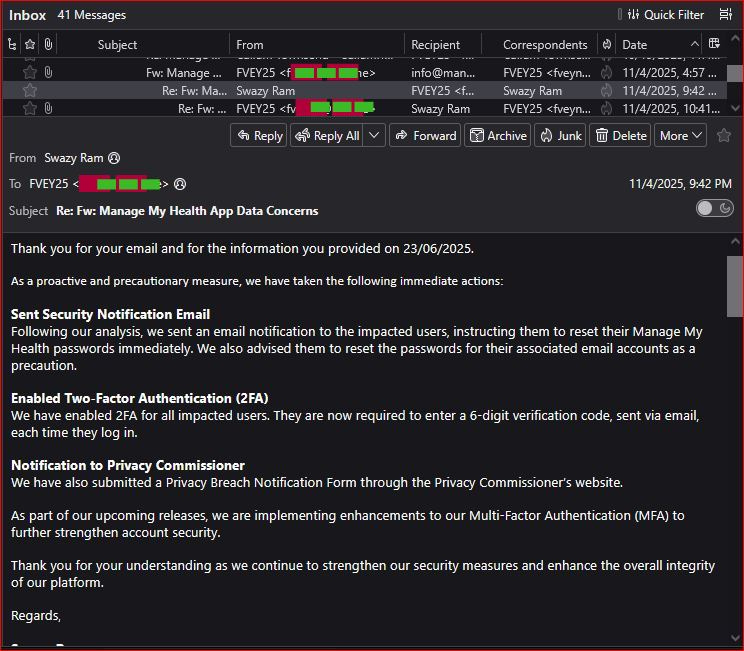
What’s concerning, is that the person from MMH that eventually responded, wasn’t the CEO or an “I.T.” professional, but a ‘Customer Care Manger’.
FVEY25 replied critically, attaching a screenshot and questioning the delay. Meanwhile, forwards continued: November 3 to RNZ’s Sam Sherwood (1 in ‘To’); November 4 to MMH support channels (3 in ‘To’), attaching the Excel leak; November 20 to Stuff Digital investigations (1 in ‘To’) and another to RNZ’s Blair (1 in ‘To’).
On November 20, Blair (possibly from Stuff or RNZ) responded: “Thanks for your email. I’ll get someone from the team to contact you.” But follow-up? Zilch.
December 2025 to January 2026: The Lie Emerges as the Breach Goes Public
Fast-forward to January 2026. MMH publicly admits a breach, with notifications starting as reported by Stuff NZ and ACS IA. They claim “discovery” on December 31, 2025—conveniently ignoring the June alerts.
FVEY25 kept pushing: January 4 forward to Minister S. Brown (1 in ‘To’); January 5 to ministers M. Doocey, C. Costello, and others (up to 5 in ‘To’ and Cc’); another to media like Kerre et al. (multiple in ‘To’ and Cc’).
By January 6, Kim Griggs from The Post News (finally replying to an email dated months prior) asked for contact details (1 in ‘To’), but FVEY25 rebuffed: “How long has it been since you, and the rest of NZ media read my emails pleading for you to DO SOMETHING about it? You’re all as much to blame...”
Forwards to RNZ’s Russell Palmer (1 in ‘To’) and more ensued, with attachments proving the timeline.
In total, these emails reached hundreds of recipients across media (Stuff, RNZ, Newstalk ZB, NZME, Infowars), government (PM Luxon, multiple ministers), intelligence (GCSB), and regulators (Privacy Commissioner staff). The sheer volume—over 300 unique contacts across chains—highlights the deliberate inaction.
The Cover-Up: Who Knew What, and When?
This isn’t incompetence; it’s a pattern. MMH’s December 31 “discovery” claim crumbles under the email evidence. The Privacy Commissioner dragged their feet, media outlets like Stuff NZ (who later reported the story without crediting early warnings) stayed silent, and PM Luxon’s office? No acknowledgment.
Why the silence? Perhaps ties to digital health initiatives. New Zealand’s government has been aggressive on digital IDs, with Health NZ pushing apps like MMH for “convenience.” But as we’ve warned in this series, centralization breeds vulnerability. This breach—potentially the largest in NZ history—affects patient records, enabling everything from blackmail to insurance fraud.
It erodes trust in any future national ID or digital driver’s license. If a health app can’t secure passwords, how can we trust a government database with our biometrics?
Call to Action: Demand Accountability
Kiwis deserve answers. Why did MMH lie about the timeline? Why did the Privacy Commissioner and GCSB (as FVEY partners, they received direct emails to over 30 staff regarding the breach, on November 18, 2025) fail to act? And why did media outlets ignore pleas until the story broke wide open?
At George News, we’re committed to exposing these truths. Share this series. To our friends down-under in New Zealand, contact your MPs, and subscribe for Parts 6 and beyond. The slippery slope isn’t hypothetical—it’s happening now.
Stay tuned, as we dig further into this story. You can bet your bottom dollar, that this won’t be the end of it.
If you have tips on this or similar stories, reach us securely via our whistleblower portal. Stay vigilant.
George News – Uncovering the stories they don’t want you to know.